As you know, WordPress is a very popular and widely used CMS for creating all kinds of websites, and it's possible to integrate plugins and themes to add functionality.
But all these elements, whether the core of WordPress or the plugins and themes, can contain vulnerabilities that can be exploited by attackers to compromise the site.
There may also be configuration issues or bad practices that can be exploited.
WPScan will therefore enable you to scan a WordPress site for the various security issues it may contain.
You can find the content of this article in video form on my YouTube channel:
Installation
WPScan is an open-source tool developed in Ruby that you can find on GitHub: https://github.com/wpscanteam/wpscan
It is also generally available in the repositories of Linux distributions. For example, on Kali Linux, you can install it with the following command:
sudo apt install wpscan
On MAC, you can install it with the following command:
brew install wpscanteam/tap/wpscan
You can also use it with Docker, which is very handy when you don't want to have to install Ruby on your machine or when you have dependency problems.
docker run -it --rm wpscanteam/wpscan --url https://target.tld/ --enumerate u
Then, to have access to all WPScan functionalities, you need to register on the WPScan website to get an API key: https://wpscan.com/api/
It's free and will give you additional details on any vulnerabilities found.
Usage
To start with, you can update WPScan with the following command:
wpscan --update
Depending on your installation, you may need sudo to update WPScan.
Here's the command I usually use to scan a WordPress site:
wpscan --url http://target.com/ --enumerate u,m,at,ap,dbe,cb, --api-token <token>
The command options are as follows:
--url: the URL of the site to be scanned--api-token: your API key--enumerate: the options for scanning the site (these are the default options, but I'm putting them here anyway to explain them)u: usersm: mediavt: Searches for installed vulnerable themesvp: Search for installed vulnerable pluginsdbe: Search for database exportscb: Search for configuration backups
We look for plugins and themes installed on the site, as they may be vulnerable, even if they are not activated. The simple fact of having them installed can allow the vulnerabilities they may contain to be exploited.
Other interesting options :
- You can use more aggressive methods to scan the site with the
--detection-mode,--plugins-detectionand--main-theme-detectionoptions. - You can also use the
--forceoption to force a scan even if the site is not detected as a WordPress site. - You can use the
--disable-tls-checksoption to disable TLS checks.
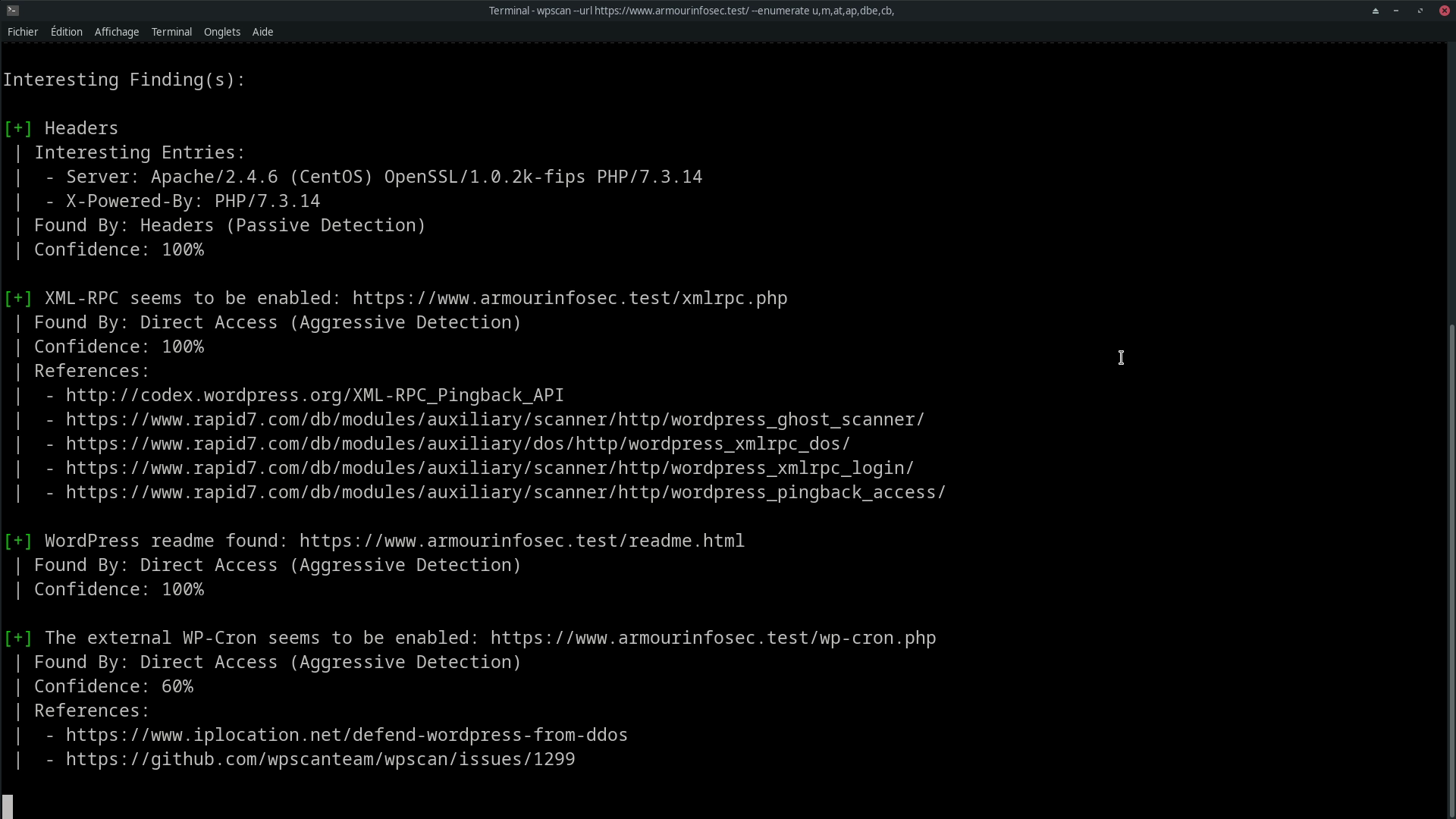
Example of results:
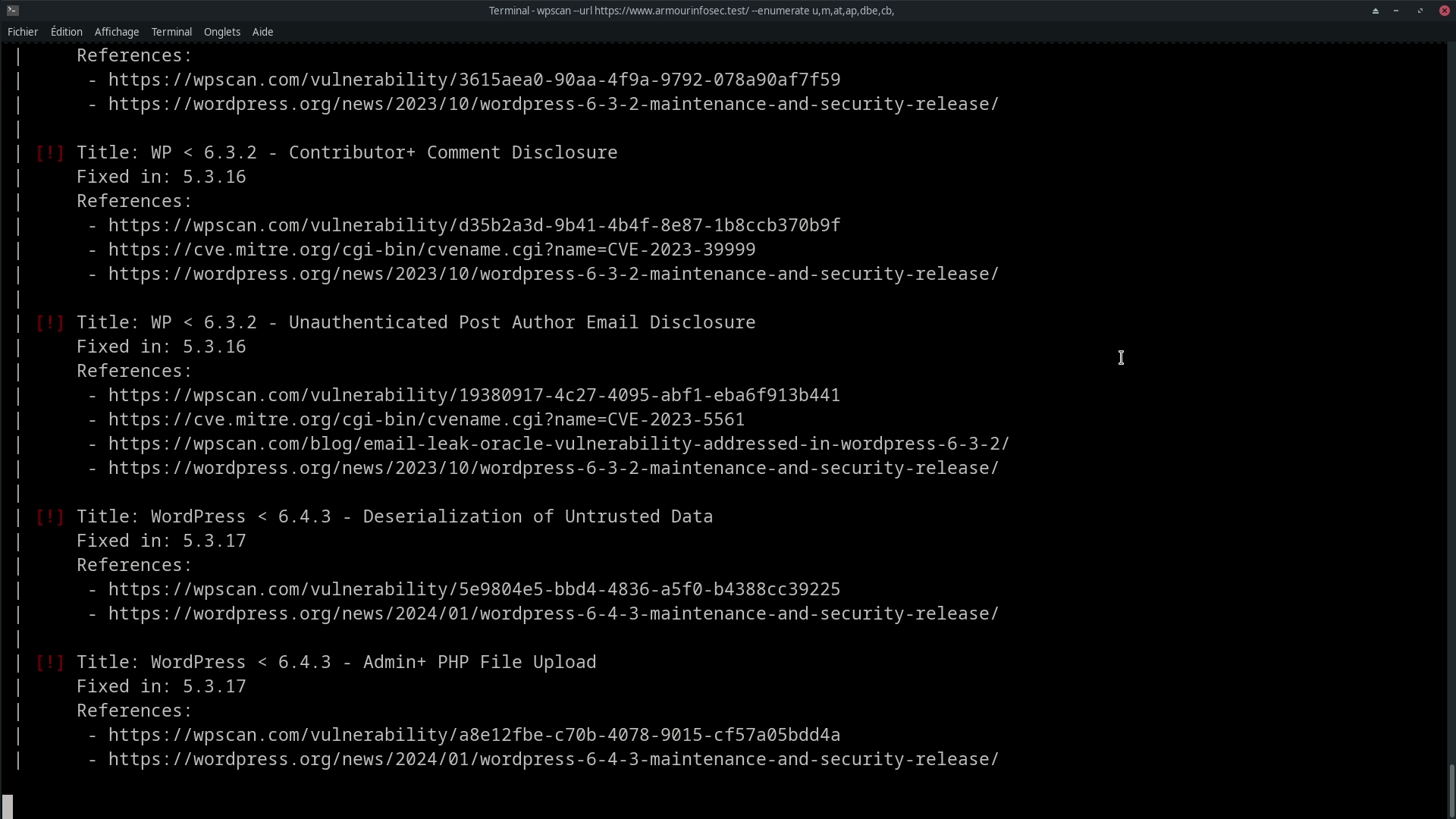
Then simply analyze the results to find the vulnerabilities you need to exploit and fix.
You can also test bruteforce attacks on users with the --passwords option.
wpscan --url example.com -e u --passwords /path/to/password_file.txt
See the WPScan documentation for more information on the available options: https://github.com/wpscanteam/wpscan/wiki/WPScan-User-Documentation
Conclusion
WPScan is an essential tool for anyone who manages WordPress sites and wants to ensure their security. By detecting potential vulnerabilities and applying the necessary patches, you can protect your site from attack.
Always remember to use WPScan ethically and legally. Make sure you have the necessary authorization before scanning a site.